个人买卖网站怎么做网络策划
1. 证书介绍
服务端保留公钥和私钥,客户端使用root CA认证服务端的公钥
一共有多少证书:
*Etcd:
- Etcd对外提供服务,要有一套etcd server证书
- Etcd各节点之间进行通信,要有一套etcd peer证书
- Kube-APIserver访问Etcd,要有一套etcd client证书
kubernetes:
- Kube-apiserver对外提供服务,要有一套kube-apiserver server证书
- kube-scheduler、kube-controller-manager、kube-proxy、kubelet和其他可能用到的组件,需要访问kube-APIserver,要有一套kube-apiserver client证书
- kube-controller-manager要生成服务的service account,要有一对用来签署service account的证书(CA证书)
- kubelet对外提供服务,要有一套kubelet server证书
- kube-apiserver需要访问kubelet,要有一套kubelet client证书
2. openssl制作证书
所需证书如下:
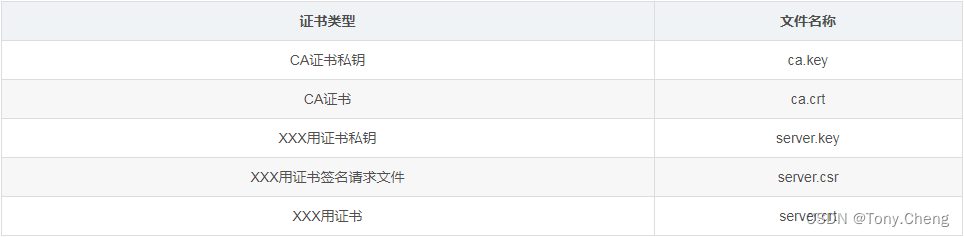
制作api-server client证书:
# ${tmpdir}为生成的临时文件夹
# tmpdir=$(mktemp -d)# 生成证书私钥
openssl genrsa -out ${tmpdir}/server-key.pem 2048# 生成csr签名文件,CN设定为域名/机器名/或者IP名称
openssl req -new -key ${tmpdir}/server-key.pem -subj "/CN=${service}.${namespace}.svc" -out ${tmpdir}/server.csr -config# 根据csr签名文件创建csr
kubectl create -f *.yaml# approve and fetch the signed certificate
kubectl certificate approve ${csrName}# 生成server-cert.pem证书文件
serverCert=$(kubectl get csr ${csrName} -o jsonpath='{.status.certificate}')
echo ${serverCert} | openssl base64 -d -A -out ${tmpdir}/server-cert.pem# 使用server-key.pem和server-cert.pem进行认证
server-key.pem
server-cert.pem
制作脚本如下:
#!/bin/bashset -e
set -xusage() {cat <<EOF
Generate certificate suitable for use with an sidecar-injector webhook service.This script uses k8s' CertificateSigningRequest API to a generate a
certificate signed by k8s CA suitable for use with sidecar-injector webhook
services. This requires permissions to create and approve CSR. See
https://kubernetes.io/docs/tasks/tls/managing-tls-in-a-cluster for
detailed explantion and additional instructions.The server key/cert k8s CA cert are stored in a k8s secret.usage: ${0} [OPTIONS]The following flags are required.--service Service name of webhook.--namespace Namespace where webhook service and secret reside.--secret Secret name for CA certificate and server certificate/key pair.
EOFexit 1
}while [[ $# -gt 0 ]]; docase ${1} in--service)service="$2"shift;;--secret)secret="$2"shiftdo;;--namespace)namespace="$2"shift;;*)usage;;esacshift
done[ -z ${service} ] && service=logsidecar-injector-admission
[ -z ${secret} ] && secret=logsidecar-injector-admission-certs
[ -z ${namespace} ] && namespace=kubesphere-logging-systemif [ ! -x "$(command -v openssl)" ]; thenecho "openssl not found"exit 1
ficsrName=${service}.${namespace}
tmpdir=$(mktemp -d)
echo "creating certs in tmpdir ${tmpdir} "cat <<EOF >> ${tmpdir}/csr.conf
[req]
req_extensions = v3_req
distinguished_name = req_distinguished_name
[req_distinguished_name]
[ v3_req ]
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[alt_names]
DNS.1 = ${service}
DNS.2 = ${service}.${namespace}
DNS.3 = ${service}.${namespace}.svc
EOFopenssl genrsa -out ${tmpdir}/server-key.pem 2048
openssl req -new -key ${tmpdir}/server-key.pem -subj "/CN=${service}.${namespace}.svc" -out ${tmpdir}/server.csr -config ${tmpdir}/csr.conf# clean-up any previously created CSR for our service. Ignore errors if not present.
kubectl delete csr ${csrName} 2>/dev/null || true# create server cert/key CSR and send to k8s API
cat <<EOF | kubectl create -f -
apiVersion: certificates.k8s.io/v1beta1
kind: CertificateSigningRequest
metadata:name: ${csrName}
spec:groups:- system:authenticatedrequest: $(cat ${tmpdir}/server.csr | base64 | tr -d '\n')usages:- digital signature- key encipherment- server auth
EOF# verify CSR has been created
while true; dokubectl get csr ${csrName}if [ "$?" -eq 0 ]; thenbreakfi
done# approve and fetch the signed certificate
kubectl certificate approve ${csrName}
# verify certificate has been signed
for x in $(seq 10); doserverCert=$(kubectl get csr ${csrName} -o jsonpath='{.status.certificate}')if [[ ${serverCert} != '' ]]; thenbreakfisleep 1
done
if [[ ${serverCert} == '' ]]; thenecho "ERROR: After approving csr ${csrName}, the signed certificate did not appear on the resource. Giving up after 10 attempts." >&2exit 1
fi
echo ${serverCert} | openssl base64 -d -A -out ${tmpdir}/server-cert.pem# create the secret with CA cert and server cert/key
kubectl create secret generic ${secret} \--from-file=key.pem=${tmpdir}/server-key.pem \--from-file=cert.pem=${tmpdir}/server-cert.pem \--dry-run -o yaml |kubectl -n ${namespace} apply -f -
